
Zero-day & signature attacks. Orchestrated attacks
Your Network's Edge®
• SaaS solution closes current security gaps
• Prevents volumetric DDoS attacks
• Faster than scrubbing centers
• Mitigation at the attack location
• AI and ML help detect even small anomalies
• Protects from inbound and outbound attacks
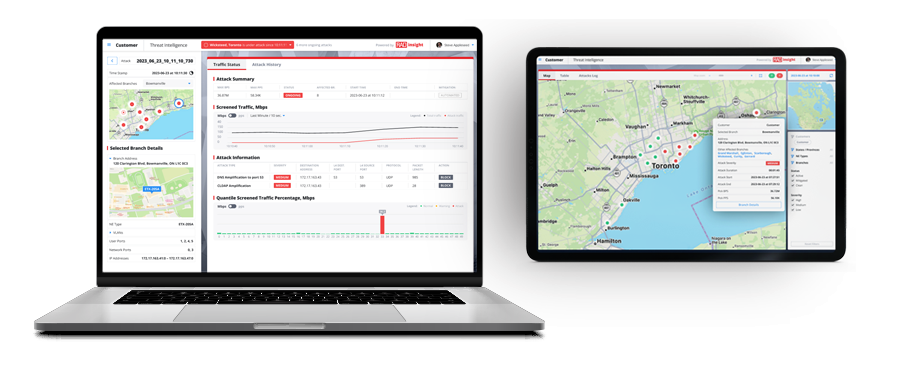
RADinsight TI detects and stops cyber-attacks within seconds. It operates via carrier and network edge devices already in your network.
The Problem with Scrubbing Centers
RADinsight complements traditional solutions that are lagging in providing protection from newer attack vectors:
RADinsight as the First Line of Defense
RADinsight TI detects and mitigates volumetric and zero-day attacks in seconds. It protects the network from starvation and is used as a first line of defense with scrubbing center activated on demand.
Operating as close as possible to the source of the attack – at L2 demarcation points and at inter-carrier demarcation points, RADinsight TI’s ML-based anomaly detection engine eliminates the need to set up a high baseline as a starting point. It can therefore detect low-volume attacks at less than 1%.
Being software-based, RADinsight TI operates without the need for traffic rerouting and without affecting device bandwidth or introducing latency.
Threat Intelligence: How It Works
RADinsight TI works by constantly collecting data from the carrier edges and monitoring all traffic to identify attacks. Once an attack is detected, closed-loop enforcement is applied via an ACL installed on the carrier edge.
Highlights
AI-driven threat intelligence with network embedded security


Zero-day & signature attacks. Orchestrated attacks

through ACL in edge devices, close to attack origin

No traffic rerouting. No additional weak point. No impact on user experience

Cloud native solution